-
0. Why/How I was Inspired to go AV free
- Like most others who have spent their working lives with computers (especially since the advent of the Internet) the idea of running a computer connected to the Internet without an Anti-Virus seemed shocking/dangerous/foolish. Then last year I ran across a couple of articles that started me thinking. Over the years I have frequently been asked to help rescue computers that were infected with malware (the current generic name for all bad-actor software - see my blog on computer security for more information on the terminology virus, malware, etc.). In almost every single case those who had a malware infection were also using a "good" anti-virus. What I should have inferred, but did not until recently, was that if the AV software was not preventing these infections, what good were they? I rationalized the issue by arguing to myself, "Yes, but if they had not had the AV running things could have been worse." Really, I must have thought that! Most of the malware I have removed in the last few years has been of the following nature: Home page hijackers, search engine hijackers, bad browser extensions, and PUPs (probably undesirable programs), none of which were caught by the installed anti-virus. I have been running without an AV on my working Windows 8.1 laptop for six months or more and have not had any infections (as confirmed by running Malwarebytes and Adwcleaner from time to time). My computer (just over three years old) is noticeably snappier in response since dispensing with the AV (I was using Avast). Of course I do have Windows Defender running. Windows will complain unless you have something in place. If you install a third-party AV it will disable Windows Defender. Here are some good articles on the issue as a whole, the first one of which got me thinking of trying it myself.
- I still don't use anti-virus software. Am I nuts?
- Disable Your Antivirus Software (Except Microsoft's) by Robert O'Callahan (former Firefox developer)
- Uninstall your antivirus: you don’t need it anymore
- Antivirus software is 'increasingly useless' and may make your computer less safe
1. A Little History of Anti-Virus Software under Windows
-
- Anti-Virus Software entry from Wikipedia with extensive notes on its history
2. Common Features and downsides of Contemporary AV Software
- One of the downsides to using any Anti-virus software is that you pay a performance penalty - this is inescapable. But there are other issues. The nature of all resident (active scanning) AV software is that it must work at a low level in the OS. You may have noticed that you have reboot your computer if you remove a resident/active AV, such as Avast. Because of this aspect of how AVs work they can become a vector to be exploited by craftily engineered virus.
The second issue is related to the first in that all software has bugs, some of which may be able to be exploited by malware. Another problem with majority of current AV is known in the software industry as "feature creep." To compete AV vendors keep adding more and more "security" features, some of which may be of dubious value and/or are poorly coded, and potentially exploitable.
For example, notice all the things Avast wants to help you with:
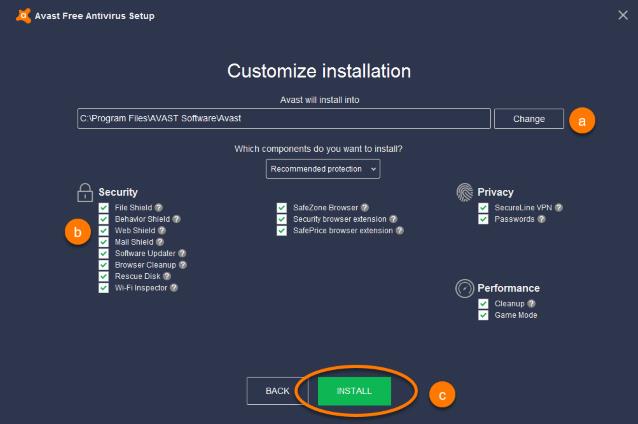
Here are some articles relevant to evaluating AV products.
- How antivirus software works: Is it worth it?
- How Antivirus Software Works
- New vulnerability uses antivirus software to infect systems with malware
- The Google Play “Super Antivirus” that’s not so super at all
3. What does Windows Defender do?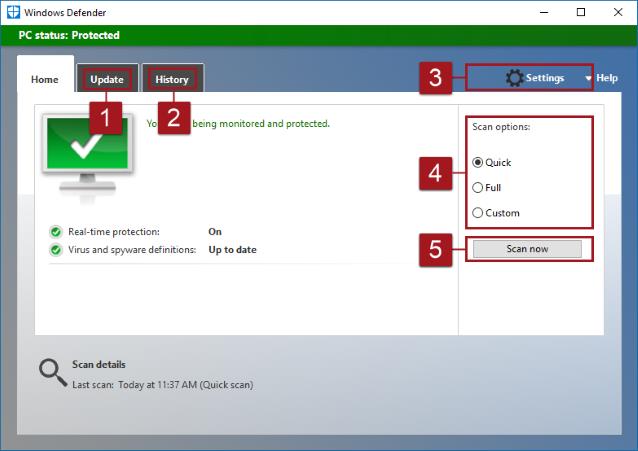
-
- Configure Windows Defender in Windows 8, 8.1 and 10
- What’s the Best Antivirus for Windows 10? (Is Windows Defender Good Enough?)
- The Windows Defender Security Center app (Windows 10)
The white paper, Anti-Virus Comparative Performance Test showed Windows Defender to caused a major performance hit compared to all other AV products. I have not seen this performance decline in my personal experience. So, YMMV.
Here's a reviewer unimpressed with Windows Defender:
- Windows Defender Review: Better Than Nothing
- Microsoft Windows Defender Security Center Review - PCMag(10/17/17)
4. Virus vectors (the elephant in the room - your browser)
-
Because it is so massively exploited, the principal virus/malware vector to be concerned about today is the browser-based infection vector. Malware infections can occur from searching for info on a topic and clicking on a link to an infected page. It can happen if you click on a "click-bait" pic/story, which is generally bogus, exaggerated or misrepresented, even on a web site that is well-known and has a "good reputation." (The ad servers that furnish the "click-bait" and pay for placement are generally kosher, but the servers themselves can and have been compromised. See 7. Ad Blocking and Malvertising below.) It can also happen by clicking a link in an email, even if the email is from a friend. (How do you KNOW it is from your friend? Email return addresses are trivial to forge.) And on and on ...
Although not in itself malware, "The 'Microsoft' Tech Support Scam" deserves special emphasis because so many people fall victim to it. I covered this topic in my presentation/blog (May 2016) on computer security, but for convenience I have added it as an addendum to this presentation. See 9. Beware Scareware below.
Very important to browser security is to make sure your browser is up-to-date:
- New Chrome/FireFox versions
The topic of distributed crytocurrency mining (a kind of bot malware) is making news and it is mostly spread by web-page infestations or perhaps rides on the back of some other application:
- How cryptocurrency mining works: Bitcoin vs. Monero
- Browser-Based Cryptocurrency Mining Makes Unexpected Return from the Dead
5. Threats that arise from OS/App/CPU vulnerabilities
-
Vulnerabilities in the OS (whether Windows, Mac X, Linux, Android, or IOS) have always been and will remain potential targets for malware. That is why it is important to keep your OS updated. Luckily Windows 10 forces updates - they are no longer optional as they were with Windows 7/8 and previous (that is, if you chose to disable automatic updates in pre-Windows 10 versions).
Since Windows is the overwhelming favorite target for malware, it goes without saying it needs to be updated routinely.
Other OSes are not quite as easy a target as Windows, partly on account of their security architecture, partly because they are much less the object of interest to nefarious hackers. Still any critical updates to any OS should not be put off. For instance there is news of this recent Apple Mac malware.
Malware can also exploit security holes in application software, such as Microsoft Office, Adobe Acrobat, Adobe Flash, Oracle's Java (although the latter is not technically an application, but rather an application framework). So these too need to be regularly updated (or removed).
New to the malware scene is a potential species of malware (so far not detected in the wild) which can attack CPUs! Two different theoretical vulnerabilities were revealed recently by Google researchers, named Meltdown (which can exploit a flaw in the design of post-1995 model Intel CPUs) and Spectre (which potentially could affect every major existing CPU platform - Intel, AMD, ARM - the later used in almost all smartphones).
- Here is the very technical article where these vulnerabilities were initially disclosed. (Warning, you will not understand this article without a degree in computer science!) I have included it for the inveterately curious. Reading privileged memory with a side-channel
Here are three much more understandable articles: - Spectre and Meltdown: Details you need on those big chip flaws
- How to protect your PC against the major ‘Meltdown’ CPU security flaw
- Mozilla Confirms Web-Based Execution Vector for Meltdown and Spectre Attacks
- ‘It Can’t Be True.’ Inside the Semiconductor Industry’s Meltdown
Also of interest - it is little known fact that AV programs can block Windows updates. This is not normally true, but in the case of the Meltdown/Spectre patch this can occur. See the following for details:
- Windows Meltdown-Spectre fix: How to check if your AV is blocking Microsoft patch
- Microsoft: No more Windows patches at all if your AV clashes with our Meltdown fix.
6. Using a browser security plug-ins vs an ad/script blocker like uBlock Origin
-
I had been using the Avast Online Security plugin (Chrome and Firefox) for some time. That is, until I came across this article:
- Don’t Use Your Antivirus’ Browser Extensions: They Can Actually Make You Less Safe
Here is the essence:
Any form of browser integration can create security holes. Antivirus programs often want to monitor all your network traffic and inspect it, but they can’t normally see what’s happening inside an encrypted connection, like the one you use to access your email, or bank, or Facebook. After all, that’s the point of encryption–to keep that traffic private. To get around this limitation, some antivirus programs effectively perform a “man-in-the-middle” attack so they can monitor what’s actually going on over an encrypted connection.
Most of these antivirus products promise to make you more secure online by blocking bad websites, and identifying bad search results. But search engines like Google already do this by default, and phishing and malware page filters are built into Google Chrome, Mozilla Firefox, and Microsoft’s web browsers. Your browser can handle itself.
Also, note well, the more extensions/plugins you use the more sluggish your browser will be.
7. Ad Blocking and Malvertising
- I have used the AdBlock Plus browser plugin to block ads for several years. In the process of doing research for presentation I discovered uBlock Origin, a cross-browser, cross OS ad blocker that has been described as an HTML firewall. It has many nice features not the least of which is its low CPU/memory footprint. Oh, and as a bonus, it vastly speeds up the loading of pages with heavy ad graphics/animations. Many web sites which depend on advertising income are now detecting the presence of the ad blocker and and either asking for you to turn it off for their site (which is easily done in UBlock Origin and AdBlock Plus) or not allowing you to see their content until you do disable it. uBlock Origin is available as a free extension for all major browsers on all major OSes, including Chrome/Firefox for Windows, Apple (Safari), Microsoft Store (Edge), and there's even an Android FireFox version. Not yet available for Android Chrome.
uBlock Origin and some other ad blockers have a behavior that will take a little getting used to. For instance assuming you don't have an ad blocker installed and you load the WRAL Weather page and then click the "Read more" in the Weather Feed column you should see a pop-up that displays the full entry for that item. However, with the ad blocker enabled, the pop-up will not be displayed. The way around this is to click on the UBlock Origin icon in your toolbar and turn off the blocking for the whole site by clicking the big blue "power" indicator or CTRL-clicking it to turn it off for the current page.
- Here is a comparative review of uBlock Origin and AdBlock Plus: uBlock Origin vs Adblock Plus: Which Is A Better Adblocker 2018?
- A PDF guide to Ad Blocking/Blockers recommends uBlock Origin.
So what does ad blocking have to do with security? If purely blocking ads, the answer is Malvertising.
I have copied the section on Malvertising from my blog on computer security here for ease of reference:
What is Malvertising?
- Malvertising Campaign Hits BBC, NYT, More
- MSN Home Page Drops More Malware Via Malvertising
And this recent (1/26/18) article shows that even major sites are not immune to a form of Malvertising:
- Now even YouTube serves ads with CPU-draining cryptocurrency miners
What to do about it:
- Malvertising Is Here: How to Protect Yourself
- Here’s why the epidemic of malicious ads grew so much worse last year: Article dated 1/23/18
Another word/phrase should be mentioned, malware scripting, which has become one of the greatest sources of malware infections in the last few years.
This is where a product like uBlock Origin is very helpful. For example, here is an example of
- uBlock Origin Developers Take Steps to Block Cryptocurrency Mining Scripts
8. Malwarebytes and Adwcleaner as a safety net
-
- Malwarebytes' Anti-Malware claims that it "Can detect and remove malware that even the most well known anti-virus and anti-malware applications fail to detect." Offers real-time protection during trial period, must be updated and run manually thereafter unless purchased. Some of the most common malware infections today (Home page hijackers, search engine hijackers, bad browser extensions, and PUPs (probably undesirable programs) are effectively dealt with by Malwarebytes (together with Adwcleaner, see below), but only after the infection unless you purchase the full version of Malwarebytes. See the PC Mag review (Dec. 2016) Also see the
short CNET review of Malwarebytes' Anti-Malware. If I were a Mac user I think I would use Malwarebytes for the Mac.
- Adwcleaner (bought by Malwarebytes last year) I call a safety net as I have had to resort to it remove infections that had gotten past major Anti-Virus programs. It detects some things that even Malwarebytes does not catch (namely PUPs). Perhaps that is why Malwarebytes bought Adwcleaner? Adwcleaner currently must be downloaded for each new version (no internal updates), and must be run manually - there is no real-time protection. Still, what it does, it does well.
9. Beware Scareware (Tech Support Scams)
- What is Scareware?
- Here is an example I captured from my own computer. It was accompanied by an irritating woman's voice repeatedly warning me I MUST call the number listed on the screen, otherwise dire things would happen to my computer! Sometimes you will hear what sounds like a fire alarm, and other emergency type sounds designed to scare you. Also you might get cold-called (from Microsoft, NOT!) telling you you have a virus on your computer - how would they know? On one person's computer which was a victim of Scareware I found that among other things the miscreants had set a DNS server address in the IPv4 properties - these servers were either down or bogus. This meant all this person's web links would fail! To them it appeared as if they were not connected to the Internet. Using a different browser would not help. Only resetting the DNS to the default (Obtain DNS server address automatically) solved this problem. Most likely someone running the uBlock Origin browser extension would not experience this problem to begin with!
- Scareware is one variety of Social Engineering
- Tech Support Scammers
- Avoid tech support phone scams
- "This is Microsoft Support" telephone scam
- Remove Tech Support Scam pop-up
- The hunt for tech support scammers
- Another wrinkle in tech support scams
- And yet another variation
- What happens if you play along with a Microsoft 'tech support' scam?
- Youtube video and commentary of a tech support scam incident
Inevitably there has grown up a host of computer techs who rejoice in posting "take downs" of tech support scammers to YouTube, as for example this one which shows how pitifully clueless these scammers can be:
- Fake Tech Support Scammer vs DarkComet (Youtube)
And this one from Norway (speaking english):
- Microsoft Scammer tries to scam a certified level 5 technician (Youtube)
|

